This website is web service for checking file that you're uploaded is the malicious file or not. It's similar Virustotal.com, try it by yourself.
Monday 23 September 2013
[Syhunt Sandcat Browser v4.1] A Penetration-oriented browser (extented to Web Application Assessment)
Sandcat Browser 4 brings unique features that are useful for pen-testers and web developers. Sandcat is built on top of Chromium, the same engine that powers the Google Chrome browser, and uses the Lua programming language to provide extensions and scripting support.
Features
- Live HTTP Headers — built-in live headers with a dedicated cache per tab and support for preview extensions
- Sandcat Console — an extensible command line console; Allows you to easily run custom commands and scripts in a loaded page
- Resources tab — allows you to view the page resources, such as JavaScript files and other web files.
- Page Menu extensions — allows you to view details about a page and more.
- Pen-Tester Tools — Sandcat comes with a multitude of pen-test oriented extensions. This includes a Fuzzer, a Script Runner, HTTP & XHR Editors, Request Loader, Request Replay capabilities and more.
Pentesting tools
- Cookies and Cache Viewers
- JavaScript Executor extension — allows you to load and run external JavaScript files
- Lua Executor extension — allows you to load and run external Lua scripts
- Page Menu extensions — allows you to view the page headers, cookies, whois information and more
- Request Editor extension with request loading capabilities
- Request Editor (Low-Level version)
- Request Viewer — allows you to view details about a request or replay a request.
- Ruby Console extension
- Sandcat Tasks (Extensions that run as isolated processes):
- Fuzzer extensions with multiple modes and support for filters
- CGI Scanner extension
- HTTP Brute Force
- Script Runner extension — can execute scripts in a variety of languages
- Tor Button extension — Anonymity for standard browsing
- XHR Editor
- Various Encoders/Decoders, new Sandcat Console commands, security related search engine options, and more
Web application hacking is based on QuickInject
QuickInject is an extensive toolkit for manual web application security assessment. QuickInject allows to tailor injection requests that you can send or load using Sandcat, and can be used for performing a number of different operations, such as URL and POST Data Manipulation, Filter Evasion, as well as Referer and User-Agent Spoofing, and HTTP Header Manipulation. In addition to the capability to build requests, QuickInject can also be used to execute JavaScript in a loaded page. The first release of QuickInject is focused on File Inclusion, XSS and SQL Injection and comes with the following options:
- SQL Injection functions
- Filter Evasion – Database-Specific String Escape (CHAR & CHR). Conversion of strings to quoted strings, conversion of spaces to comment tags or new lines
- Filter Evasion (MySQL-Specific) – String Concatenation, Percent Obfuscation & Integer Representation (eg: ’26′ becomes ‘ceil(pi()*pi())*(!!!pi()+true)+ceil(@@version)’, a technique presented by Johannes Dahse).
- UNION Statement Maker
- Quick insertion of common injections covering DB2, Informix, Ingres, MySQL, MSSQL, Oracle & PostgreSQL
- File Inclusion functions
- One-Click Log Poisoning
- Quick Shell Upload code generator
- PHP String Escape (chr)
- Cross-Site Scripting (XSS) functions
- Filter Evasion – JavaScript String Escape (String.fromCharCode), CSS Escape
- Various handy alert statements for testing for XSS vulnerabilities.
- Hash functions
- MD5 Hash Crackers – Built-in (offline) and online MD5 hash crackers
- Hash Generators – MD5, SHA-1, SHA-2 (224, 256, 384 & 512), GOST, HAVAL (various), MD2, MD4, RIPEMD (128, 160, 256 & 320), Salsa10, Salsa20, Snefru (128 & 256), Tiger (various) & WHIRLPOOL
- Encoders/Decoders
- URL Encoder/Decoder
- Hex Encoder/Decoder – Converts a string or integer to hexadecimal or vice-versa (multiple output formats supported).
- Base64 Encoder/Decoder
- CharCode Converter – Converts a string to charcodes (eg: ‘abc’ becomes ’97,98,99′) or vice-versa.
- IP Obfuscator – Converts an IP to dword, hex or octal.
- JavaScript Encoders – Such as JJEncode by Yosuke HASEGAWA
- HTML functions
- HTML Escape/Unescape
- HTML Entity Encoder/Decoder – Decimal and hexadecimal HTML entity encoders & decoders
- JavaScript String Escape
- Text Manipulation functions – Uppercase, Lowercase, Swap Case, Title Case, Reverse, Shuffle, Strip Slashes, Strip Spaces, Add Slashes, Char Separator
- Time-Based Blind Injection code – Covering MySQL, MSSQL, Oracle, PostgreSQL, Server-Side JavaScript & MongoDB
- CRC Calculators – CRC16, CRC32, CRC32b, and more.
- Classical Ciphers – ROT13 & ROT[N]
- Checksum Calculators – Adler-32 & Fletcher
- Buffer Overflow String Creator
- Random String & Number Generation functions
- URL Splitter
- Useful Strings – Math, character sets and more.
[iodine] Tunnel application to forward IPv4 traffic through DNS servers (IP over DNS)
iodine lets you tunnel IPv4 data through a DNS server. This can be usable in different situations where internet access is firewalled, but DNS queries are allowed.
It runs on Linux, Mac OS X, FreeBSD, NetBSD, OpenBSD and Windows and needs a TUN/TAP device. The bandwidth is asymmetrical with limited upstream and up to 1 Mbit/s downstream.
Compared to other DNS tunnel implementations, iodine offers:
- Higher performance
- iodine uses the NULL type that allows the downstream data to be sent without encoding. Each DNS reply can contain over a kilobyte of compressed payload data.
- Portability
- iodine runs on many different UNIX-like systems as well as on Win32. Tunnels can be set up between two hosts no matter their endianness or operating system.
- Security
- iodine uses challenge-response login secured by MD5 hash. It also filters out any packets not coming from the IP used when logging in.
- Less setup
- iodine handles setting IP number on interfaces automatically, and up to 16 users can share one server at the same time. Packet size is automatically probed for maximum downstream throughput.
[WhatWeb v0.4.7] The Content Management Systems (CMS) Technology Scanner
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 900 plugins, each to recognise something different. WhatWeb also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more.
WhatWeb can be stealthy and fast, or thorough but slow. WhatWeb supports an aggression level to control the trade off between speed and reliability. When you visit a website in your browser, the transaction includes many hints of what web technologies are powering that website. Sometimes a single webpage visit contains enough information to identify a website but when it does not, WhatWeb can interrogate the website further. The default level of aggression, called ‘passive’, is the fastest and requires only one HTTP request of a website. This is suitable for scanning public websites. More aggressive modes were developed for in penetration tests.
Most WhatWeb plugins are thorough and recognise a range of cues from subtle to obvious. For example, most WordPress websites can be identified by the meta HTML tag, e.g. ‘‘, but a minority of WordPress websites remove this identifying tag but this does not thwart WhatWeb. The WordPress WhatWeb plugin has over 15 tests, which include checking the favicon, default installation files, login pages, and checking for “/wp-content/” within relative links.
Features:
* Over 900 plugins
* Control the trade off between speed/stealth and reliability
* Plugins include example URLs
* Performance tuning. Control how many websites to scan concurrently.
* Multiple log formats: Brief (greppable), Verbose (human readable), XML, JSON, MagicTree, RubyObject, MongoDB.
* Recursive web spidering
* Proxy support including TOR
* Custom HTTP headers
* Basic HTTP authentication
* Control over webpage redirection
* Nmap-style IP ranges
* Fuzzy matching
* Result certainty awareness
* Custom plugins defined on the command line
Example Usage
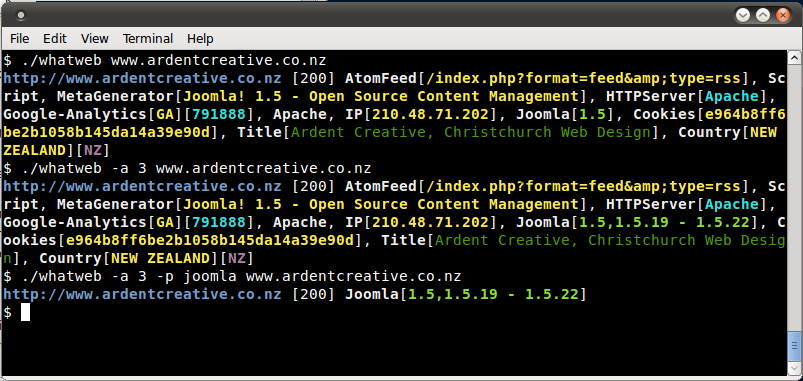
Using WhatWeb on a couple of websites:
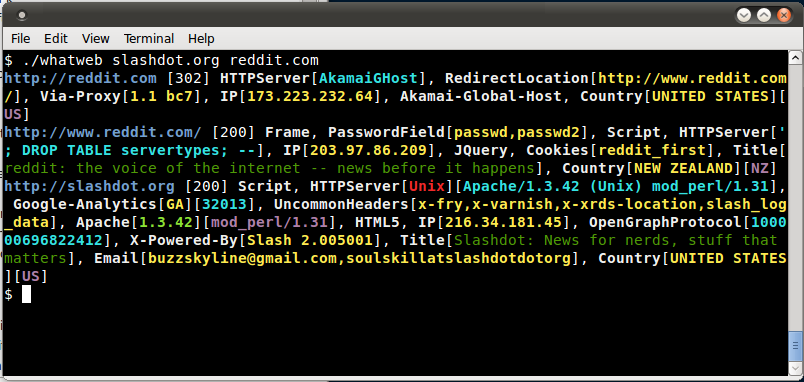
Using a higher aggression level to identify the version of Joomla in use.
[ThreatFactor NSIA v1.0.6] Network System Integrity Analysis
ThreatFactor NSIA is a website scanner that monitors websites in real-time in order to detect defacements, compliance violations, exploits, sensitive information disclosure and other issues. ThreatFactor detects issues remotely and therefore requires no software to install, does not introduce any latency and will not interrupt business operations. At it’s core, ThreatFactor uses an advanced analysis engine that is capable of detecting a wide variety of issues and can be modified with custom signatures.
NSIA can be configured perform almost any action once an issue is identified, such as sending a text message (IM, email, SMS) or executing a script.
Type of Issues Detected
The ThreatFactor solution was designed specifically to help organizations quickly identify issues on your websites that may tarnish your organization’s image or adversely affect your customers, partners and employees such as:
- Website Defacements
- Malicious users are trolling the Internet specifically for websites to deface. Oftentimes, these websites contain offensive language or images and likely result in tarnished image.
- Compliance and Privacy Issues
- ThreatFactor can detect issues that may adversely affect compliance or user privacy such as: forms that submit passwords unencrypted, pages that accept user information but don’t include a privacy policy, etc.
- Web Exploits
- Oftentimes, attackers compromise a website and install exploits to attack the website visitors. These are often classified as silent defacements since the site does not look like it was visually changed. Sophos noted that the vast majority of websites hosting malware (around 80%) are legitimate sites that have been compromised . Furthermore, ThreatFactor can detect websites that have been modified in such a way to send private customer information (such as login information) to a third party.
- Sensitive Information Leaks
- Websites can leak sensitive information through detailed error messages, misinformed blogger employees, and files that were not intended to be provided to the public.
- System Failures
- ThreatFactor can detect many types of website system problems such as:
- Broken Links
- Error and warning messages
- Poorly configured servers or servers with default configuration
- Expired SSL certificates
- Server errors
Key Features
- Automatic Content Baselining and Self-Tuning
- ThreatFactor automatically creates analyzes monitored sites and establishes a baseline; the baseline is used to self-tune the system in order to reduce the rate of false alerts and to increase the sensitivity to potentially unauthorized changes.
- Automatic Web-Content Discovery
- ThreatFactor automatically discovers the content associated with monitored websites; oftentimes finding hidden or unexpected content.
- Built-In Web Interface
- ThreatFactor features an built-in web-server that makes administration easy using a web-browser.
- Comprehensive Signature Set
- Includes over 2000 signatures for issues ranging from exploits and privacy problems to offensive language.
- Full Access Controls
- The ThreatFactor servers supports rights, object-level access controls that can be applied to users and groups.
- Integrated Custom Signature Editor
- A syntax highlighting signature editor is provided for writing custom ThreatPattern and ThreatScript signatures.
- SIEM Integration
- ThreatFactor can log to a an external device such as a Security Information Event Management (SIEM) tool or log management solution.
- Integrated Database
- ThreatFactor features an integrated database and eliminates the need for a DBA.
[vFeed & vFeed API] The open source cross-linked local vulnerability database
 vFeed is an open source naming scheme concept that provides extra structured detailed 3rd parties references for a CVE entry. While the emergence of the Open Standards helped undeniably to shape a new way to communicate about vulnerabilities1, the new vFeed is adding an intelligent structured xml feed that provides effective level of information (meta-data) related to vulnerability.
vFeed is an open source naming scheme concept that provides extra structured detailed 3rd parties references for a CVE entry. While the emergence of the Open Standards helped undeniably to shape a new way to communicate about vulnerabilities1, the new vFeed is adding an intelligent structured xml feed that provides effective level of information (meta-data) related to vulnerability.Internally, vFeedCore (not published yet) collects the basis xml feeds which are generated by reliable references and correlates it across multiple information sources. Here are examples of 3rd parties sources (just to name a few):
- Security standards
- CVE (http://cve.mitre.org)
- CWE (http://cwe.mitre.org)
- CPE (http://cpe.mitre.org)
- OVAL (http://oval.mitre.org)
- CAPEC (http://capec.mitre.org)
- CVSS (http://www.first.org/cvss)
- Vulnerability Assessment & Exploitation IDs (Metasploit, Saint Corporation, Nessus Scripts, ZDI, Exploit-DB, milw0rm)
- Vendors Security Alerts
- Microsoft MS
- Mandriva
- Redhat
- Cisco
- Sun
- Gentoo
- Apple
- ...
Key features
- Built using open source technologies
- Fully downloadable SQLite local vulnerability database
- Structured new XML format to describe vulnerabilities
- Based on major open standards CVE, CPE, CWE, CVSS..
- Support correlation with 3rd party security references (CVSS, OSVDB, OVAL…)
- Extended to support correlation with security assessment and patch vendors (Nessus, Exploit-DB, Redhat, Microsoft..)
- Simple & ready to use Python module with more than 15 methods
Target Audience
- Penetration testers who want to analyze CVEs and gather extra information to help shape avenues to exploit vulnerabilities.
- Security auditors who want to report accurate information about findings. vFeed could be the best way to describe a CVE with attributes based on standards and 3rd party references as vendors or companies involved into standarization efforts.
- Security tools vendors / security open source developers who need to implement libraries to enumerate useful information about CVEs without wasting time to correlate and to create a proprietary database. vFeed is by far the best solution. Methods can be invoked from programs or scripts with a simple call.
- Any security hacker who is conducting researches and need a very fast and accurate way to enumerate available exploits or techniques to check a vulnerability
Friday 20 September 2013
[JBrute v0.9.4] Open Source Security tool to audit hashed passwords
JBrute is an open source tool written in Java to audit security and stronghold of stored password for several open source and commercial apps. It is focused to provide multi-platform support and flexible parameters to cover most of the possible password-auditing scenarios.
Java Runtime version 1.7 or higher is required for running JBrute.
Features
- Muli-platform support (by Java VM)
- Several hashing algorithms supported
- Flexible chained hashes decryption (like MD5(SHA1(MD5())))
- Both brute force and dictionary decryption methods supported
- Build-In rule pre-processor for dictionary decryption
- Multi-threading support for brute force decryption
Supported algorithms:
- MD5
- MD4
- SHA-256
- SHA-512
- MD5CRYPT
- SHA1
- ORACLE-10G
- ORACLE-11G
- NTLM
- LM
- MSSQL-2000
- MSSQL-2005
- MSSQL-2012
- MYSQL-322
- MYSQL-411
- POSTGRESQL
- SYBASE-ASE1502
[ollydbg-binary-execution-visualizer] New Tool for Visualizing Binaries With Ollydbg and Graphvis
Sometimes crackme’s or something you might be reversing will constantly bug you due to the excessive usage of f7 & f8. It will be quiet neat if you can see how the application is executing visually and set your break points accordingly.
Requirements:
o Ollyscript plugin
o Bunch of your favorite anti-‐debug plugins (phantom , ollyadvanced, …etc) o Pygraphviz
o Graphviz
o Python 2.7
Approach:
- Create an ollyscript that will do the followingo Log all EIP for main applicationo Disregard to log calls to kernel32 , ntdll & addresses which are above
7C000000 using step over not step into include more addresses toexclude if needed later for other system dll’s 77000000 … etc. o Save EIP Logs to file - Parse the log file
- Feed it into pygraphviz
- Export to png
- Visualize & note needed breakpoints.
- Re-‐run the app setting above breakpoints.
[Arachni v0.4.5.1-0.4.2] Open Source Web Application Security Scanner Framework
Arachni is a Free/Open Source project, the code is released under the Apache License Version 2.0 and you are free to use it as you see fit.
Initially started as an educational exercise, it has since evolved into a powerful and modular framework allowing for fast, accurate and flexible security/vulnerability assessments. More than that, Arachni is highly extend-able allowing for anyone to improve upon it by adding custom components and tailoring most aspects to meet most needs.
New Changes
- Optimized pattern matching to use less resources by grouping patterns to only be matched against the per-platform payloads. Bottom line, pattern matching operations have been greatly reduced overall and vulnerabilities can be used to fingerprint the remote platform.
- Modules
- Path traversal ( path_traversal)
- Updated to use more generic signatures.
- Added dot-truncation for MS Windows payloads.
- Moved non-traversal payloads to the file_inclusion module.
- File inclusion ( file_inclusion) — Extracted from path_traversal.
- Uses common server-side files and errors to identify issues.
- SQL Injection ( sqli) — Added support for the following databases:
- Firebird
- SAP Max DB
- Sybase
- Frontbase
- IngresDB
- HSQLDB
- MS Access
- localstart_asp — Checks if localstart.asp is accessible.
- Path traversal ( path_traversal)
- Plugins — Added:
- Uncommon headers ( uncommon_headers) — Logs uncommon headers.

[OWASP Zed Attack Proxy 2.2.1] Tool for finding vulnerabilities in web applications (Now supports CWE)
 OWASP Zed Attack Proxy (ZAP) An easy to use integrated penetration testing tool for finding vulnerabilities in web applications. It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to an experienced pen testers toolbox.
OWASP Zed Attack Proxy (ZAP) An easy to use integrated penetration testing tool for finding vulnerabilities in web applications. It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to an experienced pen testers toolbox.Some of ZAP’s features:
- Intercepting Proxy
- Automated scanner
- Passive scanner
- Brute Force scanner
- Spider
- Fuzzer
- Port scanner
- Dynamic SSL certificates
- API
- Beanshell integration
Some of ZAP’s characteristics:
- Easy to install (just requires java 1.6)
- Ease of use a priority
- Comprehensive help pages
- Fully internationalized
- Under active development
- Open source
- Free (no paid for ‘Pro’ version)
- Cross platform
- Involvement actively encouraged
Monday 16 September 2013
[Binrev] Automate Reversing Windows Binaries for Pentesters
 What you can do with this?
What you can do with this?- Static analysis: you can do a basic manual code review for decompiled sources to discover hidden communication channels, search for hard-coded passwords, or SQL injection vulnerabilities.
- Import decompiled projects to an IDE to reconstruct and modify the original source code
- Call hidden native exported functions with rundll32
Here is a rough description of what it does, and what tools it is using:
- For exe, dll files:
- Detect and de-obfuscate for .NET libraries with de4dot
- Decompile .NET libraries with JustDecompile
- Zip decompiled source code to netsources.zip
- Run strings against native libraries
- Export call-able functions with dllexp. You can then try to run those functions with command Rundll32 <dll>,<function name>
- Export dependencies with depends
- Extract native resources with resourcesextract
- For jar files:
- Extract and combine java classes into a single zip file
- Decompile java sources with procyon
- Zip decompiled source code to javasources.zip
Forensics Tools
ADQUISICIÓN Y ANÁLISIS DE LA MEMORIA
pd Proccess Dumper - Convierte un proceso de la memoria a fichero.
FTK Imager - Permite entre otras cosas adquirir la memoria.
DumpIt - Realiza volcados de memoria a fichero.
Responder CE - Captura la memoria y permite analizarla.
Volatility - Analiza procesos y extrae información util para el analista.
RedLine - Captura la memoria y permite analizarla. Dispone de entrono gráfico.
Memorize - Captura la ram (Windows y OSX).
Set de utilidades que permite la adquisición de la memoria ram para posteriormente hacer un análisis con ella.
pd Proccess Dumper - Convierte un proceso de la memoria a fichero.
FTK Imager - Permite entre otras cosas adquirir la memoria.
DumpIt - Realiza volcados de memoria a fichero.
Responder CE - Captura la memoria y permite analizarla.
Volatility - Analiza procesos y extrae información util para el analista.
RedLine - Captura la memoria y permite analizarla. Dispone de entrono gráfico.
Memorize - Captura la ram (Windows y OSX).
MONTAJE DE DISCOS
Utilidades para montar imágenes de disco o virtualizar unidades de forma que se tenga acceso al sistema de ficheros para posteriormente analizarla.
ImDisk - Controlador de disco virtual.
OSFMount - Permite montar imágenes de discos locales en Windows asignando una letra de unidad.
raw2vmdk - Utilidad en java que permite convertir raw/dd a .vmdk
FTK Imager - Comentada anteriormente, permite realizar montaje de discos.
vhdtool - Convertidor de formato raw/dd a .vhd permitiendo el montaje desde el administrador de discos de Windows .
LiveView - Utilidad en java que crea una máquina virtual de VMware partiendo de una imagen de disco.
MountImagePro - Permite montar imágenes de discos locales en Windows asignando una letra de unidad
CARVING Y HERRAMIENTAS DE DISCO
Recuperación de datos perdidos, borrados, búsqueda de patrones y ficheros con contenido determinado como por ejemplo imágenes, vídeos. Recuperación de particiones y tratamiento de estructuras de discos.
PhotoRec - Muy útil, permite la recuperación de imágenes y vídeo.
Scalpel -Independiente del sistema de archivos. Se puede personalizar los ficheros o directorios a recuperar.
RecoverRS - Recupera urls de acceso a sitios web y ficheros. Realiza carving directamente desde una imágen de disco.
NTFS Recovery - Permite recuperar datos y discos aún habiendo formateado el disco.
Recuva - Utilidad para la recuperación de ficheros borrados.
Raid Reconstructor - Recuperar datos de un RAID roto, tanto en raid 5 o raid 0. Incluso si no conocemos los parámetros RAID.
CNWrecovery - Recupera sectores corruptos e incorpora utilidades de carving.
Restoration - Utilidad para la recuperación de ficheros borrados.
Rstudio - Recuperación de datos de cualquier sistema de disco NTFS, NTFS5, ReFS, FAT12/16/32, exFAT, HFS/HFS+ (Macintosh), Little y Big Endian en sus distintas variaciones UFS1/UFS2 (FreeBSD/OpenBSD/NetBSD/Solaris) y particiones Ext2/Ext3/Ext4 FS.
Freerecover - Utilidad para la recuperación de ficheros borrados.
DMDE - Admite FAT12/16, FAT32, NTFS, y trabaja bajo Windows 98/ME/2K/XP/Vista/7/8 (GUI y consola), DOS (consola), Linux (Terminal) e incorpora utilidades de carving.
IEF - Internet Evidence Finder Realiza carving sobre una imagen de disco buscando mas de 230 aplicaciones como chat de google, Facebook, IOS, memoria ram, memoria virtual,etc.
Bulk_extractor - Permite extraer datos desde una imagen, carpeta o ficheros.
UTILIDADES PARA EL SISTEMA DE FICHEROS
Conjunto de herramientas para el análisis de datos y ficheros esenciales en la búsqueda de un incidente.
analyzeMFT - David Kovar's utilidad en python que permite extraer la MFT
MFT Extractor- Otra utilidad para la extracción de la MFT
INDXParse - Herramienta para los indices y fichero $I30.
MFT Tools (mft2csv, LogFileParser, etc.) Conjunto de utilidades para el acceso a la MFT
MFT_Parser - Extrae y analiza la MFT
Prefetch Parser - Extrae y analiza el directorio prefetch
Winprefectchview - Extrae y analiza el directorio prefetch
Fileassassin - Desbloquea ficheros bloqueados por los programas
ANÁLISIS DE MALWARE
PDF Tools de Didier Stevens.
PDFStreamDumper - Esta es una herramienta gratuita para el análisis PDFs maliciosos.
SWF Mastah - Programa en Python que extrae stream SWF de ficheros PDF.
Proccess explorer - Muestra información de los procesos.
Captura BAT - Permite la monitorización de la actividad del sistema o de un ejecutable.
Regshot - Crea snapshots del registro pudiendo comparar los cambios entre ellos
Bintext - Extrae el formato ASCII de un ejecutable o fichero.
LordPE - Herramienta para editar ciertas partes de los ejecutables y volcado de memoria de los procesos ejecutados.
Firebug - Analisis de aplicaciones web.
IDA Pro - Depurador de aplicaciones.
OllyDbg - Desemsamblador y depurador de aplicaciones o procesos.
Jsunpack-n - Emula la funcionalidad del navegador al visitar una URL. Su propósito es la detección de exploits
OfficeMalScanner - Es una herramienta forense cuyo objeto es buscar programas o ficheros maliciosos en Office.
Radare - Framework para el uso de ingeniería inversa.
FileInsight - Framework para el uso de ingeniería inversa.
Volatility Framework con los plugins malfind2 y apihooks.
shellcode2exe - Conversor de shellcodes en binarios.
FRAMEWORKS
Captura BAT - Permite la monitorización de la actividad del sistema o de un ejecutable.
Regshot - Crea snapshots del registro pudiendo comparar los cambios entre ellos
Bintext - Extrae el formato ASCII de un ejecutable o fichero.
LordPE - Herramienta para editar ciertas partes de los ejecutables y volcado de memoria de los procesos ejecutados.
Firebug - Analisis de aplicaciones web.
IDA Pro - Depurador de aplicaciones.
OllyDbg - Desemsamblador y depurador de aplicaciones o procesos.
Jsunpack-n - Emula la funcionalidad del navegador al visitar una URL. Su propósito es la detección de exploits
OfficeMalScanner - Es una herramienta forense cuyo objeto es buscar programas o ficheros maliciosos en Office.
Radare - Framework para el uso de ingeniería inversa.
FileInsight - Framework para el uso de ingeniería inversa.
Volatility Framework con los plugins malfind2 y apihooks.
shellcode2exe - Conversor de shellcodes en binarios.
FRAMEWORKS
Conjunto estandarizado de conceptos, prácticas y criterios en base a el análisis forense de un caso.
PTK - Busca ficheros, genera hash, dispone de rainbow tables. Analiza datos de un disco ya montado.
Log2timeline - Es un marco para la creación automática de un super línea de tiempo.
Plaso - Evolución de Log2timeline. Framework para la creación automática de un super línea de tiempo.
OSForensics - Busca ficheros, genera hash, dispone de rainbow tables. Analiza datos de un disco ya montado.
DFF - Framework con entorno gráfico para el análisis.
SANS SIFT Workstation - Magnifico Appliance de SANS. Lo utilizo muy a menudo.
Autopsy - Muy completo. Reescrito en java totalmente para Windows. Muy útil.
ANÁLISIS DEL REGISTRO DE WINDOWS
DFF - Framework con entorno gráfico para el análisis.
SANS SIFT Workstation - Magnifico Appliance de SANS. Lo utilizo muy a menudo.
Autopsy - Muy completo. Reescrito en java totalmente para Windows. Muy útil.
ANÁLISIS DEL REGISTRO DE WINDOWS
Permite obtener datos del registro como usuarios, permisos, ficheros ejecutados, información del sistema, direcciones IP, información de aplicaciones.
RegRipper - Es una aplicación para la extracción, la correlación, y mostrar la información del registro.
WRR - Permite obtener de forma gráfica datos del sistema, usuarios y aplicaciones partiendo del registro.
WRR - Permite obtener de forma gráfica datos del sistema, usuarios y aplicaciones partiendo del registro.
Shellbag Forensics Análisis de los shellbag de windows.
Registry Decoder - Extrae y realiza correlación aun estando encendida la máquina datos del registro.
HERRAMIENTAS DE RED
WireShark - Herramienta para la captura y análisis de paquetes de red.
NetworkMiner - Herramienta forense para el descubrimiento de información de red.
Netwitness Investigator - Herramienta forense. La versión 'free edition' está limitado a 1GB de tráfico.
Network Appliance Forensic Toolkit - Conjunto de utilidades para la adquisición y análisis de la red.
Xplico - Extrae todo el contenido de datos de red (archivo pcap o adquisición en tiempo real). Es capaz de extraer todos los correos electrónicos que llevan los protocolos POP y SMTP, y todo el contenido realizado por el protocolo HTTP.
Snort - Detector de intrusos. Permite la captura de paquetes y su análisis.
Splunk - Es el motor para los datos y logs que generan los dispositivos, puestos y servidores. Indexa y aprovecha los datos de las generados por todos los sistemas e infraestructura de IT: ya sea física, virtual o en la nube.
AlientVault - Al igual que Splunk recolecta los datos y logs aplicándoles una capa de inteligencia para la detección de anomalías, intrusiones o fallos en la política de seguridad.
RECUPERACIÓN DE CONTRASEÑAS
Registry Decoder - Extrae y realiza correlación aun estando encendida la máquina datos del registro.
HERRAMIENTAS DE RED
Todo lo relacionado con el tráfico de red, en busca de patrones anómalos, malware, conexiones sospechosas, identificación de ataques, etc.
WireShark - Herramienta para la captura y análisis de paquetes de red.
NetworkMiner - Herramienta forense para el descubrimiento de información de red.
Netwitness Investigator - Herramienta forense. La versión 'free edition' está limitado a 1GB de tráfico.
Network Appliance Forensic Toolkit - Conjunto de utilidades para la adquisición y análisis de la red.
Xplico - Extrae todo el contenido de datos de red (archivo pcap o adquisición en tiempo real). Es capaz de extraer todos los correos electrónicos que llevan los protocolos POP y SMTP, y todo el contenido realizado por el protocolo HTTP.
Snort - Detector de intrusos. Permite la captura de paquetes y su análisis.
Splunk - Es el motor para los datos y logs que generan los dispositivos, puestos y servidores. Indexa y aprovecha los datos de las generados por todos los sistemas e infraestructura de IT: ya sea física, virtual o en la nube.
AlientVault - Al igual que Splunk recolecta los datos y logs aplicándoles una capa de inteligencia para la detección de anomalías, intrusiones o fallos en la política de seguridad.
RECUPERACIÓN DE CONTRASEÑAS
Todo lo relacionado con la recuperación de contraseñas en Windows, por fuerza bruta, en formularios, en navegadores.
Ntpwedit - Es un editor de contraseña para los sistemas basados en Windows NT (como Windows 2000, XP, Vista, 7 y 8), se puede cambiar o eliminar las contraseñas de cuentas de sistema local. No valido para Active Directory.
Ntpasswd - Es un editor de contraseña para los sistemas basados en Windows, permite iniciar la utilidad desde un CD-LIVE
pwdump7 - Vuelca los hash. Se ejecuta mediante la extracción de los binarios SAM.
SAMInside / OphCrack / L0phtcrack- Hacen un volcado de los hash. Incluyen diccionarios para ataques por fuerza bruta.
DISPOSITIVOS MÓVILES
Esta sección dispone de un set de utilidades y herramientas para la recuperación de datos y análisis forense de dispositivos móviles. He incluido herramientas comerciales dado que utilizo algunas de ellas y considero que son muy interesantes e importantes.
iPhone
iPhoneBrowser - Accede al sistema de ficheros del iphone desde entorno gráfico.
iPhone Analyzer - Explora la estructura de archivos interna del iphone.
iPhoneBackupExtractor - Extrae ficheros de una copia de seguridad realizada anteriormente.
iPhone Backup Browser - Extrae ficheros de una copia de seguridad realizada anteriormente.
iPhone-Dataprotection - Contiene herramientas para crear un disco RAM forense, realizar fuerza bruta con contraseñas simples (4 dígitos) y descifrar copias de seguridad.
iPBA2 - Accede al sistema de ficheros del iphone desde entorno gráfico.
sPyphone - Explora la estructura de archivos interna.
BlackBerry
BlackBerry
Blackberry Desktop Manager - Software de gestión de datos y backups.
Phoneminer - Permite extraer, visualizar y exportar los datos de los archivos de copia de seguridad.
Blackberry Backup Extractor - Permite extraer, visualizar y exportar los datos de los archivos de copia de seguridad.
MagicBerry - Puede leer, convertir y extraer la base de datos IPD.
Android
Android
android-locdump. - Permite obtener la geolocalización.
androguard - Permite obtener, modificar y desensamblar formatos DEX/ODEX/APK/AXML/ARSC
viaforensics - Framework de utilidades para el análisis forense.
viaforensics - Framework de utilidades para el análisis forense.
Osaf - Framework de utilidades para el análisis forense.
PRODUCTOS COMERCIALES
PRODUCTOS COMERCIALES
No podían faltar. Disponer de estas herramientas es una maravilla y un lujo el poder utilizarlas. Rápidas y concisas. Lo peor en alguna de ellas es el precio.
XRY (http://www.msab.com)
Mobilyze (http://www.blackbagtech.com)
SecureView2 (http://mobileforensics.susteen.com)
MobilEdit! (http://www.mobiledit.com)
Oxygen Forensic (http://www.oxygen-forensic.com)
CellDEK (http://www.logicube.com)
Mobile Phone Examiner (http://www.accessdata.com)
Lantern (http://katanaforensics.com)
Device Seizure (http://www.paraben.com)
Neutrino (www.guidancesoftware.com)
[Capture the flag] Remaster Linux Live CD images for wargames
Remaster Linux Live CD images for the purpose of creating ready to use security wargames with pre-installed vulnerabilities to exploit.
Requirements
You will need the following in order to build the Live CD using the scripts in this project:- Linux, with root access using
sudo gitmake,gcc-- for building vulnerable programspwgen-- for generating random passwordsrsyncgenisoimage-- formkisofsadvancecomp-- foradvdefsquashfs-tools-- forunsquashfscurl-- for downloading packages and other files
[SuperPutty Password Decryptor] SuperPutty Session Login Password Recovery Software
SuperPutty Password Decryptor is the Free desktop tool to instantly recover all the login passswords from SuperPutty session history.
SuperPutty is a Windows GUI Application that allows PuTTY SSH Client to be opened in Tabs. It also stores the session details allowing users to automatically login without entering the password every time.
SuperPutty Password Decryptor helps you to quickly recover all the stored login passwords from this session file. It also automatically detects SuperPutty session file for the current user and displays it. Alternatively, you can also select another session file copied from remote system.
After the successful recovery, you can generate detailed password report in HTML/XML/TEXT file. It is very simple and easy to use tool with its cool GUI interface.
[sslnuke] SSL without verification isn't secure!
 We have all heard over and over that SSL without verification is not secure. If an SSL connection is not verified with a cached certificate, it can easily be hijacked by any attacker. So in 2013, one would think we had totally done away with this problem. Browsers cache certificates and very loudly warn the user when a site has offered up a self-verified certificate and should not be trusted, browser vendors have pretty much solved this problem. However, HTTPS is not the only protocol that uses SSL. Unfortunately, many clients for these other protocols do not verify by default and even if they did, there is no guarantee of secure certificate transfer. After all, how many people are willing to pay $50 for an SSL certificate for their FTPS server?
We have all heard over and over that SSL without verification is not secure. If an SSL connection is not verified with a cached certificate, it can easily be hijacked by any attacker. So in 2013, one would think we had totally done away with this problem. Browsers cache certificates and very loudly warn the user when a site has offered up a self-verified certificate and should not be trusted, browser vendors have pretty much solved this problem. However, HTTPS is not the only protocol that uses SSL. Unfortunately, many clients for these other protocols do not verify by default and even if they did, there is no guarantee of secure certificate transfer. After all, how many people are willing to pay $50 for an SSL certificate for their FTPS server?A common protocol that uses SSL but is rarely verified is IRC. Many IRC clients verify by default, but most users will turn this off because IRC servers administrators tend not to purchase legitimate SSL certificates. Some popular clients even leave SSL verification off by default (IRSSI, for example). We already know that this is unwise, any attacker between a user and the IRC server can offer an invalid certificate and decrypt all of the user's traffic (including possibly sensitive messages). Most users don't even consider this fact when connecting to an SSL "secured" IRC server.
The purpose of sslnuke is to write a tool geared towards decrypting and intercepting "secured" IRC traffic. There are plenty of existing tools that intercept SSL traffic already, but most of these are geared towards HTTP traffic. sslnuke targets IRC directly in order to demonstrate how easy it is to intercept "secured" communications. sslnuke usage is simple.
[OS X Auditor] free Mac OS X computer forensics tool
OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you want to analyze:
- the kernel extensions
- the system agents and daemons
- the third party's agents and daemons
- the old and deprecated system and third party's startup items
- the users' agents
- the users' downloaded files
- the installed applications
It extracts:
- the users' quarantined files
- the users' Safari history, downloads, topsites, HTML5 databases and localstore
- the users' Firefox cookies, downloads, formhistory, permissions, places and signons
- the users' Chrome history and archives history, cookies, login data, top sites, web data, HTML5 databases and local storage
- the users' social and email accounts
- the WiFi access points the audited system has been connected to (and tries to geolocate them)
It also looks for suspicious keywords in the .plist themselves.
It can verify the reputation of each file on:
- Team Cymru's MHR
- VirusTotal
- Malware.lu
- your own local database
It can aggregate all logs from the following directories into a zipball:
- /var/log (-> /private/var/log)
- /Library/logs
- the user's ~/Library/logs
Finally, the results can be:
- rendered as a simple txt log file (so you can cat-pipe-grep in them… or just grep)
- rendered as a HTML log file
- sent to a Syslog server
Friday 13 September 2013
[SpearPhisher] A Simple Phishing Email Generation Tool
SpearPhisher is a simple point and click Windows GUI tool designed for (mostly) non-technical people who would like to supplement the education and awareness aspect of their information security program. Not only is it useful to non-technical folks, penetration testers may find it handy for sending quick and easy ad-hoc phishing emails. The tool supports specifying different sending names and email addresses, multiple recipients via TO, CC, BCC, and allows bulk loading with one recipient email address per line in a file. It allows customization of the subject, adding one attachment, and SSL support for SMTP enabled mail servers. One of the popular features with our client is the WYSIWYG HTML editor that allows virtually anyone to use the tool; previewing results as you point and click edit your malicious email body. If you want to add custom XSS exploits, client side attacks, or other payloads such as a Java Applet code generated by the Social Engineer Toolkit (SET), its split screen editor allows more advanced users to edit HTML directly.
[OWASP ZAP] Herramienta de Pentest para encontrar vulnerabilidades en aplicaciones web
OWASP ZAP, una de las herramientas absolutamente indispensable en el arsenal de cualquier pentester, acaba de liberar su versión 2.2.0
Esta fabulosa herramienta, que además es gratuita, no para de progresar y añadir nuevas funcionalidades. Un enorme ¡GRACIAS! a OWASP por hacer que el proyecto crezca y siga adelante.
Esta versión trae interesantes novedades como por ejemplo soporte para Mozilla Zest, un motor de scripting orientado a herramientas de seguridad en entornos web.
Así mismo también han integrado soporte para 'Plug-n-Hack', un estándar promovido por Mozilla para definir una forma elegante y funcional de integrar herramientas de seguridad en el navegador.
Adicionalmente se han hecho -literalmente- un montón de correcciones de fallos y se han añadido nuevas funcionalidades, se puede consultar la lista entera aquí
Y luce tal que así
Fuente: http://www.securitybydefault.com/
[SecureCheq v1.0] The Security Configuration Management made easy!
SecureCheq is a fast, simple utility for Windows servers and desktops that answers these questions while it tests for common configuration risks. This free utility:
- Tests for a subset of typical (and often dangerous) Windows configuration errors
- Provides detailed remediation and repair advice
- Tests for about two dozen critical but common configuration errors related to OS hardening, Data Protection, Communication Security, User Account Activity and Audit Logging.
- Demonstrates how systems can be continually hardened against attack
SecureCheq uses configuration tests just like the ones defined in CIS, ISO or COBIT standards. Because these tests include helpful links back to comparable tests in governing policies like DISA, HIPAA or NERC, you can easily see how well your target system would fare under these policies.
Security Configuration Management isn’t easy – it needs to continually balance risk and productivity – but it is possible. And it can be one of your most cost-effective options for cyber defense.
SecureCheq supports these Windows versions and platforms:
- Windows Server 2003
- Windows Server 2008
- Windows XP
- Windows 7
- Windows 8
- Windows Server 2012
Sunday 8 September 2013
[OWASP Broken Web Applications Project VM v1.1] Collection of vulnerable web applications
 The Broken Web Applications (BWA) Project is a collection of vulnerable web applications that is distributed on a Virtual Machine.
The Broken Web Applications (BWA) Project is a collection of vulnerable web applications that is distributed on a Virtual Machine.The Broken Web Applications (BWA) Project produces a Virtual Machine running a variety of applications with known vulnerabilities for those interested in:
- Learning about web application security
- Testing manual assessment techniques
- Testing automated tools
- Testing source code analysis tools
- Observing web attacks
- Testing WAFs and similar code technologies
- All the while saving people interested in doing either learning or testing the pain of having to compile, configure, and catalog all of the things normally involved in doing this process from scratch.
Changelog v1.1 (2013-07-30)
- Updated Mutillidae, Cyclone, and WAVSEP.
- Updated OWASP Bricks and configured it to pull from SVN.
- Fixed ModSecurity CRS blocking and rebuilt ModSecurity to include LUA support.
- Increased VM’s RAM allocation to 1Gb.
- Set Tomcat to run as root (to allow some traversal issues tested by WAVSEP).
- Updated landing page for OWASP 1-Liner to reflect that the application is not fully functional.
More Information: here
[Kautilya v0.4.4] Pwnage with Human Interface Devices
Kautilya is a toolkit which provides various payloads for Teensy device which may help in breaking in a computer. The toolkit is written in Ruby.
- The Windows payloads and modules are written mostly in powershell (in combination with native commands) and are tested on Windows 7.
- The Linux payloads are mostly commands in combination with little Bash scripting. These are tested on Ubuntu 11.
Changelog v0.4.4
- Added “Download and Execute Powershell Script” windows payload.
- Added “Remove Update” windows payload.
- Added “LSA Secrets” windows payload.
- Updated “DNS TXT Backdoor”. It is much more easy to use know.
- Renamed Wait for Command to HTTP Backdoor
- HTTP Backdoor now keeps running till the stopstring is matched.
- An option has been added for no exfiltration of data. Choose 0 when Kautilya asks for exfil option.
Full Changelog: here
[Facebook Password Dump] Tool to instantly recover your lost Facebook password
Facebook Password Dump is the command-line tool to instantly recover your lost Facebook password from popular web browsers and messengers.
It automatically discovers installed applications on your system and recovers all the stored Facebook login passwords within seconds.
Being command-line tool makes it ideal tool for penetration testers and forensic investigators. For GUI version check out the Facebook Password Decryptor.
[wEAPe] Weape-Wireless-EAP-Extractor Script
Auto extracts EAP 802.1x user names
Features
- Sets up wireless card into monitor mode
- Lists all APs
- Associates with AP's you wish
- Extracts domain user names from any connects using EAP
Requirements
- airodump tool set
[Nimbostratus] Tools for fingerprinting and exploiting Amazon cloud infrastructures
Nimbostratus are tools for fingerprinting and exploiting Amazon cloud infrastructures. Nimbostratus is the first toolset to help you in the process of pivoting in Amazon AWS clouds
Features
- Enumerate permissions to AWS services for current IAM role
- Use poorly configured IAM role to create new AWS user
- Extract local and remote AWS credentials from metadata, .boto, etc.
- Clone DB to access information stored in snapshot
- Inject raw Celery task for pickle attack
If you need help understanding what this toolset is all about, Andres Riancho wrote an article “Pivoting in Amazon clouds“.
More Information: here
[Bluebox-ng] UC/VoIP Security Tool
 Bluebox-ng is a next generation UC/VoIP security tool. It has been written in CoffeeScript using Node.js powers. This project is "our 2 cents" to help to improve information security practices in VoIP/UC environments.
Bluebox-ng is a next generation UC/VoIP security tool. It has been written in CoffeeScript using Node.js powers. This project is "our 2 cents" to help to improve information security practices in VoIP/UC environments.- GitHub repo: https://github.com/jesusprubio/bluebox-ng
- IRC(Freenode): #breakingVoIP
Install
GNU/Linux and Mac OS X
- Install Node.js:
- cd bluebox-ng
- chmod +x setup.sh (just in case)
- ./setup.sh
- ./bluebox.sh
Windows
- Install Node.js: http://nodejs.org/download/
- Install Gow (the lightweight alternative to Cygwin): https://github.com/bmatzelle/gow/wiki
- cd bluebox-ng
- chmod +x setup.sh (just in case)
- setup.sh
- bluebox.sh
Features
- RFC compliant
- TLS and IPv6 support
- SIP over websockets (and WSS) support (draft-ietf-sipcore-sip-websocket-08)
- SHODAN, exploitsearch.net and Google Dorks
- SIP common security tools (scan, extension/password bruteforce, etc.)
- REGISTER, OPTIONS, INVITE, MESSAGE, SUBSCRIBE, PUBLISH, OK, ACK, CANCEL, BYE and Ringing requests support
- Authentication through different types of requests
- SIP denial of service (DoS) testing
- SRV and NAPTR discovery
- Dumb fuzzing
- Common VoIP servers web management panels discovery
- Automatic exploit searching (Exploit DB, PacketStorm, Metasploit)
- Automatic vulnerability searching (CVE, OSVDB, NVD)
- Geolocation
- Colored output
- Command completion
- It runs in GNU/Linux, Mac OS X and Windows
[(D)DoS Deflate] Script designed to block a denial of service attack
(D)DoS Deflate is a lightweight bash shell script designed to assist in the process of blocking a denial of service attack. It utilizes the command below to create a list of IP addresses connected to the server, along with their total number of connections. It is one of the simplest and easiest to install solutions at the software level.
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nIP addresses with over a pre-configured number of connections are automatically blocked in the server's firewall, which can be direct iptables or Advanced Policy Firewall (APF). (We highly recommend that you use APF on your server in general, but deflate will work without it.)
Notable Features
- It is possible to whitelist IP addresses, via /usr/local/ddos/ignore.ip.list.
- Simple configuration file: /usr/local/ddos/ddos.conf
- IP addresses are automatically unblocked after a preconfigured time limit (default: 600 seconds)
- The script can run at a chosen frequency via the configuration file (default: 1 minute)
- You can receive email alerts when IP addresses are blocked.
Subscribe to:
Posts (Atom)




















DoS+Deflate.gif)